Protocol Support
Some dissectors, like TCP, consume a significant amount of CPU, memory, and storage. It is recommended to use them for debugging purposes.
Kubeshark supports a wide variety of modern protocols, with new protocols being added frequently. Kubeshark captures all L4 traffic related to the list of targeted pods. This traffic includes TCP and UDP. Traffic from pods that aren’t targeted isn’t captured.
See the Capture Filters section to learn more about how pods are targeted.
Once traffic is captured, Kubeshark attempts to identify the protocol and starts dissecting and reassembling the API call based on the protocol specifications. If Kubeshark is unable to identify the protocol, the traffic is discarded and not presented.
Check out the list of supported protocols in the introduction section.
Read our TLS (eBPF) documentation to learn how Kubeshark deals with encrypted traffic.
The list of available protocol dissectors can be configured. Removing redundant protocols can serve two purposes:
- Reducing the level of noise.
- Improving resource consumption, as Kubeshark will process less traffic that may be less relevant (e.g.,
dns).
Dynamically Configuring Available Dissectors
The dashboard provides a way to dynamically set, enable, and disable the supported protocol dissectors.
Once pressed, the available dissectors will appear in a modal dialog window, allowing you to enable or disable them.
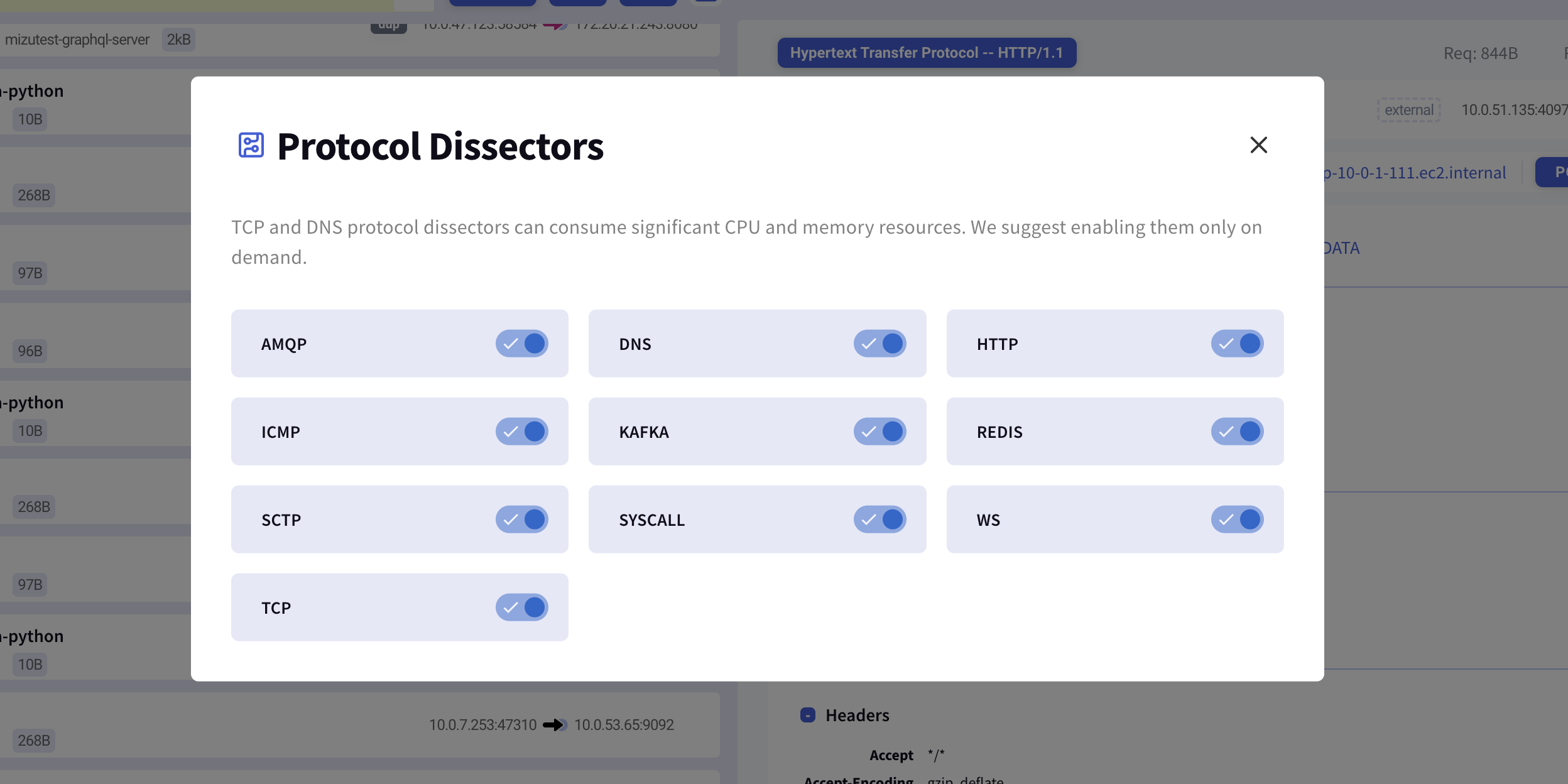
Default Configuration
By editing the enabledDissectors section in the values.yaml file, you can select which protocol dissectors will be made available. In the example below, only dns and http are kept as available protocol dissectors, with the rest disabled.
tap:
enabledDissectors:
#- amqp
- dns
- http
# - icmp
# - kafka
# - redis
# - sctp
# - syscall
# - tcp
# - wsAlternatively, you can use a Helm command line argument indicating the protocols you’d like to process. In this example, Kubeshark will process http, dns, and tcp only:
--set-json 'tap.enabledDissectors=["http","dns","tcp"]'To disable a dissector, simply remove it from the list.
This version corrects typos and clarifies some of the language while retaining the original intent.